We all know, but always find an excuse to postpone them - the dreaded security updates.
Unfortunately, there are a group of people who like to, for whatever reason, be it to boast amongst their peers or want to run some elaborate scheme for their own purposes. With the rise of anti-virus solutions readily available, these people now turn to what is known as a zero-day exploit to gain access to computers on a global scale. It doesn't help they are published in real time for the hacking community to take advantage of. While exploits are addressed quickly, it is still the responsibility of the end user to actually install them.
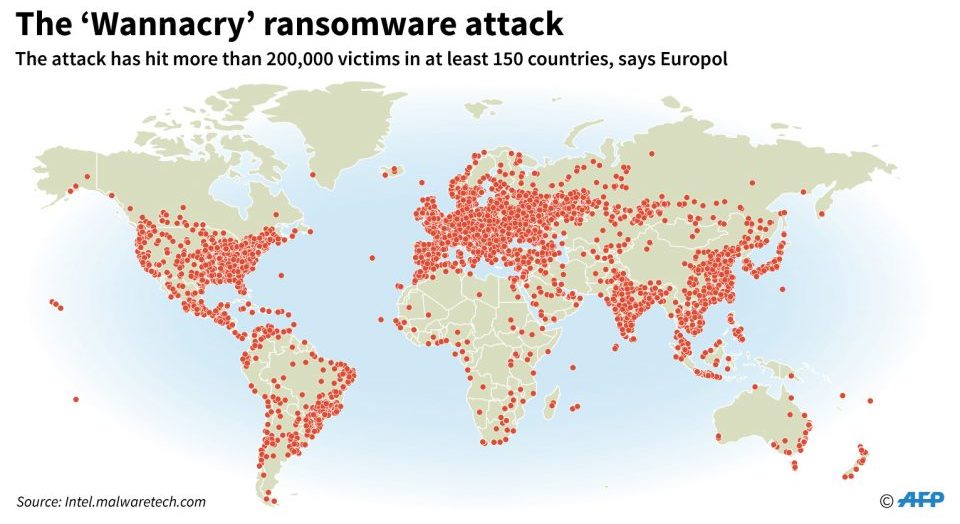
In May 2017, a group of hackers built ransomware called WannaCry which propagated using a Windows Server exploit called EternalBlue, demanding bitcoins in exchange for releasing precious data files that are taken hostage via strong encryption. Quite aggressively, it took out critical systems across many sectors - ranging from patient care systems in the NHS (national health service) in the United Kingdom to revenue raising Speed Cameras in Australia.
While bringing the distribution of WannaCry simply required the registration of a domain name - it hasn't taken long for hackers to create a new incarnation based on the same exploit. Petya, six weeks after the WannaCry attack is now spreading across the globe after originating from computer systems within the Ukraine. Similar to WannaCry; the software demands bitcoins as payment to recover data files it encrypts on the infected systems.
While Petya has apparently tried to learn from WannaCry's mistakes - it seems the developer forgot to secure the domain of the email address (wowsmith123456@posteo.net) to receive ransom demands, the account has since been disabled - meaning all users that have been affected will not be able to get their files back even if they pay the ransom.
We are yet to see the extent of the damage that has been caused from these ransomware attacks; nor should we expect them to be the last. Microsoft has posted security updates to systems all the way back to Windows XP - if you haven't applied these updates already, it should be the first thing you do after reading this entry.
Linux and Mac OSX users are also not exempt from hacking; installing security updates on a regular basis should be mandatory - even for embedded devices like Raspberry Pi and mobile phones, as they can also be vulnerable to attack.

