Should we really put so much trust into the manufacturers of security solutions?

We took the liberty of attending SecTech 2017 held at the Stockholmässan in Stockholm on the 21-22 November 2017, as they had a seminar section on IoT and security while at the same time we could get an idea of what the current manufacturers of security solutions (video surveillance, alarms, smart locks et al) have to offer on the market. It also gave us a chance to bring up some recent security exploits and their position on how to handle them.
While the majority of security exploits are based on human stupidity (not much we can do); such as default passwords, sometimes there are legitimate cases where a security exploit, such as SQL / OS command injections or 0-day vulnerabilities - found in the wild requires a modification and a subsequent firmware update to be released. Typically; the hacking community is nice to provide sufficient warning before publishing such vulnerabilities allowing vendors to release a patch or firmware update in time to prevent mass hacking.
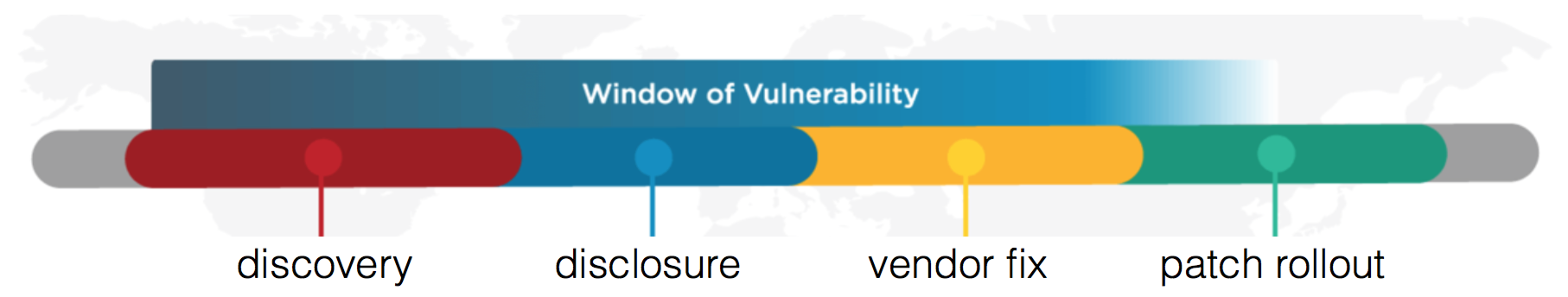
In general; there is a "Window of Vulnerability" where devices that have a known exploit could potentially be vulnerable to attack. In a perfect world; an exploit is discovered, it is disclosed with the manufacturer and the researchers sets a dealing for the manufacturer to provide a fix and patch the issue before they disclose their findings to the public.
It is only natural; that device manufacturers would take this initiative to confirm the vulnerability and then provide an appropriate fix that can be deployed to the customers devices in the wild - in most cases, the majority of vendors do; but what is their stance on getting the new firmware announced and ensure that it is deployed on existing devices?
We took approached a representative of one vendor at the conference about this:
Q: Once a firmware update is announced; what happens? A: We publish an announcement and contact our distributors to inform end-users. Q: What if the distributor doesn't contact the end-user? Q: Do you expect the end-user to know how to install a firmware update? Q: Have you considered the ability to push updates automatically to the devices? A: We have considered it; but decided not to due to privacy and trust issues. A: Our goal is to educate users that they need to keep their devices updated. Q: So theoretically; even after an update - millions of devices are vulnerable? A: I guess so, we require the users to install updates when available.
We will not disclose the vendor we talked to (no need to name and shame); but, we expect the same answer from all vendors on this exact topic. They simply build hardware, provide it to distributors to sell it and hope the end-user is tech savvy enough to install an update if one is available. The focus is sales and rolling out the next version as a hardware upgrade.
Now; there is a potential business model here - the companies that installed the cameras could notify the end-user and say "hey, there is a critical update for your cameras, you can perform the update yourself or pay us $$$ to visit your premises and do it for you". The majority of end-users would be mad, expecting it to be fixed for free - as technically it is fault in the product that was sold. It seems the onus is on the end-user entirely.
Let's consider a different market completely. If the air-bag of your new car is deemed to be dysfunctional; a massive recall annoucement will be made to allow the customer to return the vehicle to the dealer to get the air-bag replaced at the manufacturers cost to ensure that no-one is critically injured from a faulty product - a completely different approach.
Why isn't there the same policy for IT security solutions?
Exactly who should be liable when the loss or damage to property is due to a security exploit in a product that is supposed to provide security for such property; but fails to deliver on that promise? We may still be in the infant stages of such technology; but something needs to be done to ensure that devices are simply not deployed and forever left vulnerable - the responsibility should be on the vendors, not the end-user.
Should vendors be looking at providing device management services for their customers - to ensure that the latest firmware versions exist on their device. Even if not providing automatic updates; at least provide a means of contacting the customer directly (email, phone) to seek assistance in doing an update for their products on their own or via third parties.

